

Chapter 5 Security Configuration
Jaguar Manager allows you to set the quality of protection (QOP) for Jaguar packages, components, and methods. QOP establishes a minimum level of encryption and authentication that a client must meet before it can access your business logic. For example, if you do not set a QOP at the package level, all clients can access the package. You can then set a QOP that restricts access to components within that package, and a different QOP that further restricts access to methods within those components.
![]() This document discusses setting server-side QOP. For
information about configuring client-side QOP, see the Jaguar
CTS Programmer's Guide.
This document discusses setting server-side QOP. For
information about configuring client-side QOP, see the Jaguar
CTS Programmer's Guide.
The client's QOP, Jaguar listener's security profile, and the package/ component/method QOP work together to establish end-to-end security. To accommodate naming services and reduce connection time, a special CORBA component tag is set in the interoperable object reference (IOR). The naming service sends only profiles with QOPs that match a client's QOP so that the client tries to access only listeners and packages/components/methods for which the client has a compatible QOP.
See "Interoperable object references" for information about IORs.
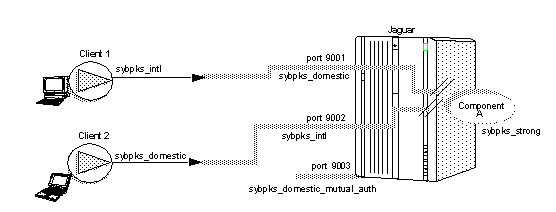
Figure 5-2 illustrates two clients trying to access component A. A QOP of sybpks_strong is set for the component. To access the component, the client must use a QOP that meets the minimum requirements of the component's QOP, and communicate with a listener that also meets the minimum requirements of the component's QOP. In Figure 5-2:
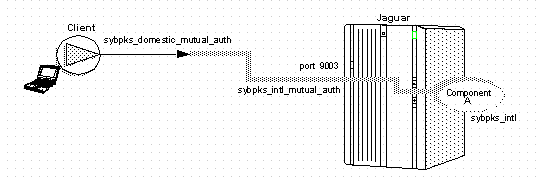
Assuming that a compatible listener is configured on the server, Figure 5-4 illustrates a situation in which the client:
Setting a weaker QOP at the method than the component serves no purpose since the client will already be blocked at the component.
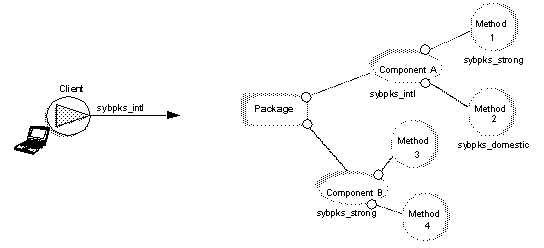
In addition to setting a QOP that establishes minimum encryption requirements, Jaguar provides another QOP, syb_osauth, for operating system authentication. You can set two QOP settings at the package, component, or method level, as long as one of them is syb_osauth:
![]() For syb_osauth to work properly,
you must enable operating-system- based authorization server-wide
(not at the listener level). If you do not, you cannot load packages,
components, or methods that have the syb_osauth QOP set.
See "Administration password and
OS authentication" for information
about enabling authorization for your operating system.
For syb_osauth to work properly,
you must enable operating-system- based authorization server-wide
(not at the listener level). If you do not, you cannot load packages,
components, or methods that have the syb_osauth QOP set.
See "Administration password and
OS authentication" for information
about enabling authorization for your operating system.
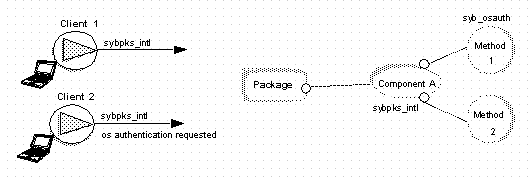
In Figure 5-5:
![]() Configuring QOP from Jaguar Manager
Configuring QOP from Jaguar Manager
Highlight the package, component, or method for which you want to establish a QOP.
com.sybase.package.qop
property
for a package.
com.sybase.component.qop
property
for a component.
com.sybase.method.qop
property
for a method.
After configuring QOP, you must either refresh or restart the server for your changes to take effect.
Table 5-8 provides a hiearchy of QOP settings. For a given client to access your business logic:
QOP hierarchy from weaker to stronger |
Comments |
|---|---|
syb_osauth |
Some QOP profiles overlap. For example, sybpks_domestic supports both 128-bit encryption and 40-bit encryption. If you use sybpks_domestic as a package QOP, a client QOP of sybpks_intl meets the minimum requirement of 40-bit encryption. sybpks_strong supports only 128-bit encryption and is compatible with only one of the domestic or strong profiles. For a list of CipherSuites supported by each QOP profile, see Table 5-4. |
| Copyright © 2000 Sybase, Inc. All rights reserved. |

| |